RSA前端js加密 后端java解密

什么是RSA加密
RSA加密是一种非对称加密算法,其具体实现如下:
1、选择两个不相等的质数p和q,计算n=pq
2、计算n的欧拉函数φ(n)=(p-1)(q-1)
3、选择一个整数e,1<e<φ(n),且e与φ(n)互质
4、计算d, 使得(d*e)modφ(n)=1
5、公钥是(n, e),私钥是(n, d)
6、加密时,将明文m^e mod n,解密时,将密文c^d mod n
例如公钥(n, e) = (33, 3),私钥(n, d) = (33, 7),明文m = 24,加密后的密文c = 24^3 mod 33 = 24,解密后的明文m = 24^7 mod 33 = 24
p = 11, q = 3, n = 33, φ(n) = 20, e = 3, d = 7
前端js加密
1 | npm install jsencrypt |
生成公钥和私钥
1 | import forge from 'node-forge' |
前端加密
1 | import Encrypt from 'jsencrypt'; |
后端解密
1 | import org.springframework.stereotype.Service; |
存在的问题 当前端解密信息超长时jsencrypt库无法分段加密
1 | // 将数据替换为以下数据即会显示Message too long for RSA 原因:RSA 加密算法对单个消息块的长度有限制。这是因为 RSA 加密使用公钥对消息进行加密,而消息的长度不能超过密钥的长度减去填充字节数。因此对于 1024 位(128 字节)的 RSA 密钥,最大消息长度为:128 - 11 - 3 = 128 - 14 = 117 |
解决方法使用encryptlong库
1 | npm install encryptlong |
验证
1 | import JSEncrypt from 'encryptlong'; |
后端可以解析 but 当内容过长且出现中文时后端就会解析失败😭 例如加密输入改为:
1 | let data = { |
后端解析报错
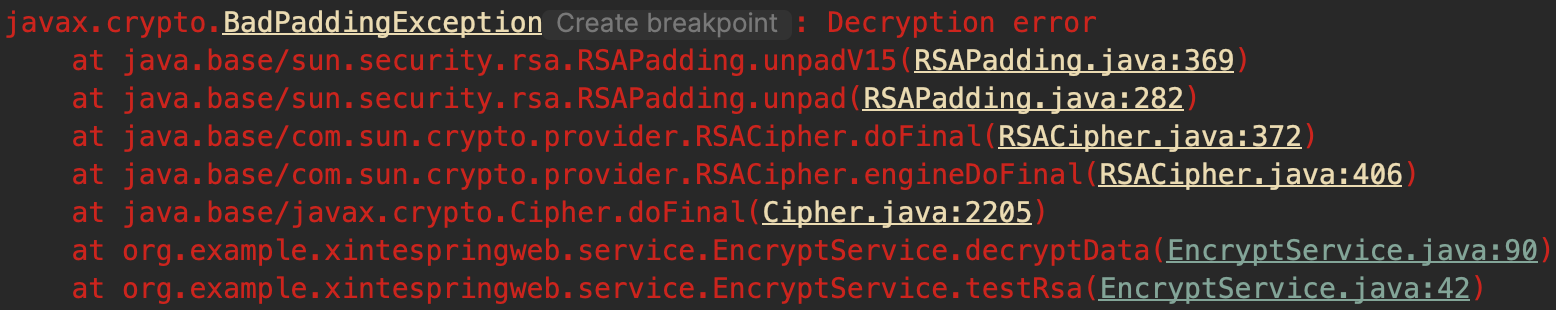
原因排查 源码解析
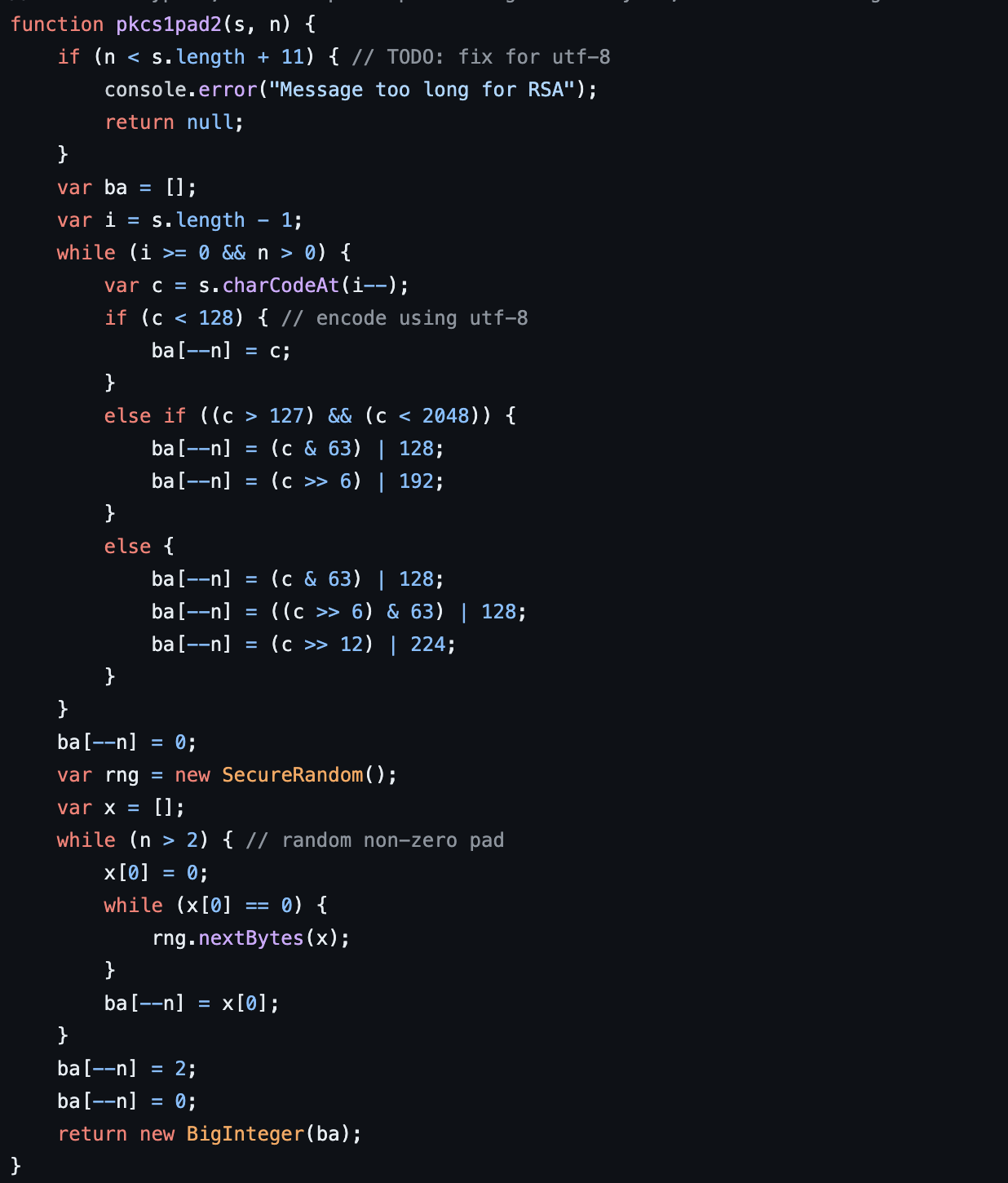
PKCS#1 v1.5 填充方案
PKCS#1 v1.5 是一种填充方案,用于确保 RSA 加密的安全性和一致性。它在加密前对数据进行填充,以确保填充后的数据长度与 RSA 密钥长度相匹配。具体填充格式如下:
1 | 0x00 || 0x02 || PS || 0x00 || D |
代码中体现
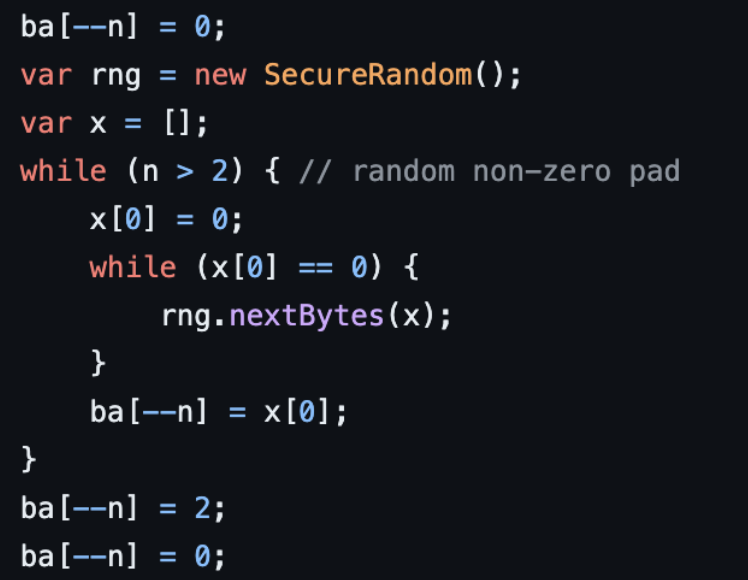
中文问题:
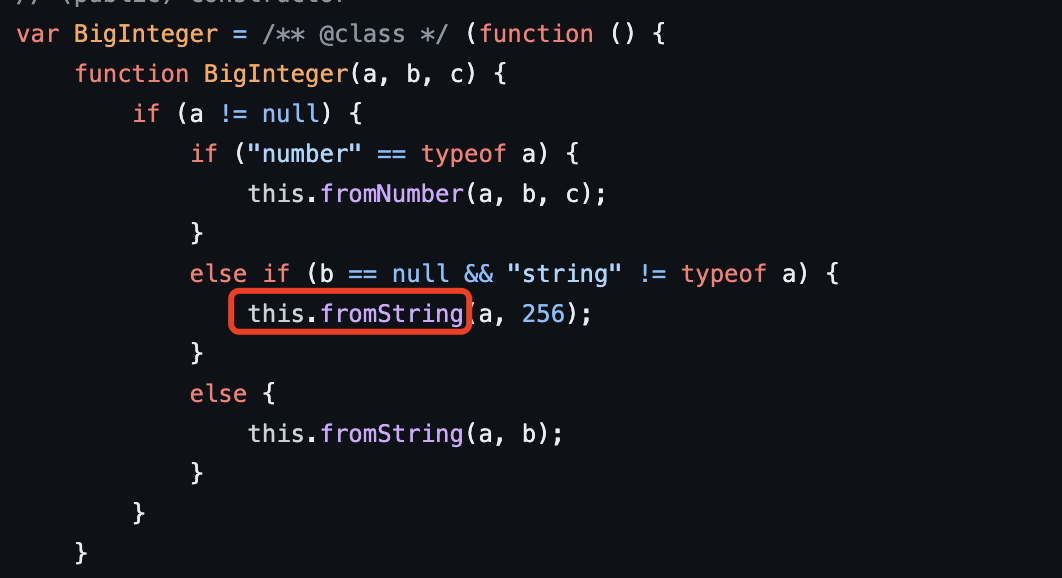
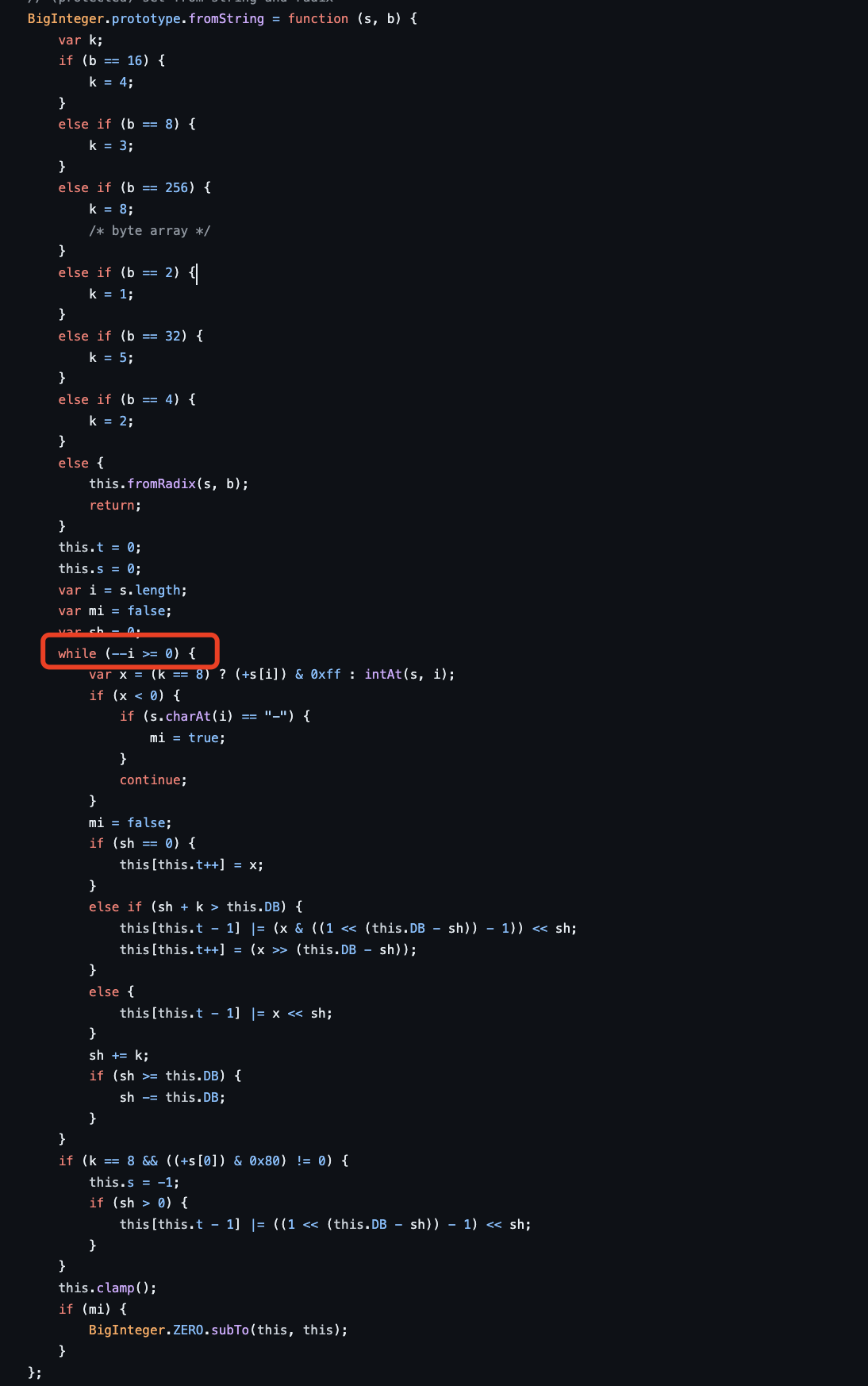
当出现中文时由于其占3个字符 所以会导致传入的ba数组出现负索引的情况 导致后续解密失败
https://www.npmjs.com/package/jsencrypt-ext
使用这位大哥改进的代码就可以,但是我在使用其打包构建后的文件script导入仍有问题。
评论